Start your journey in the amazing world of cybersecurity right now, on your own pace and in your own home!
In Hakatemia you will learn cybersecurity, ethical hacking and programming from professionals. You start from the basics and soon you will be practicing real attacks safely in a training environment. The Hakatemia community supports you on your journey.
Hakatemia members stories
Here are some nice things people have said about us ❤️
Level up!
Gamified learning environment
Hakatemia is a gamified learning environment where you get experience points, levels and badges for successfully completing tasks. On the leaderboard, you can compete with other students.
Complete tasks to level up
By completing tasks you get experience points and levels.
Master new skills
Hakatemia has different types of exercises that give experience points to the skills related to the exercise.
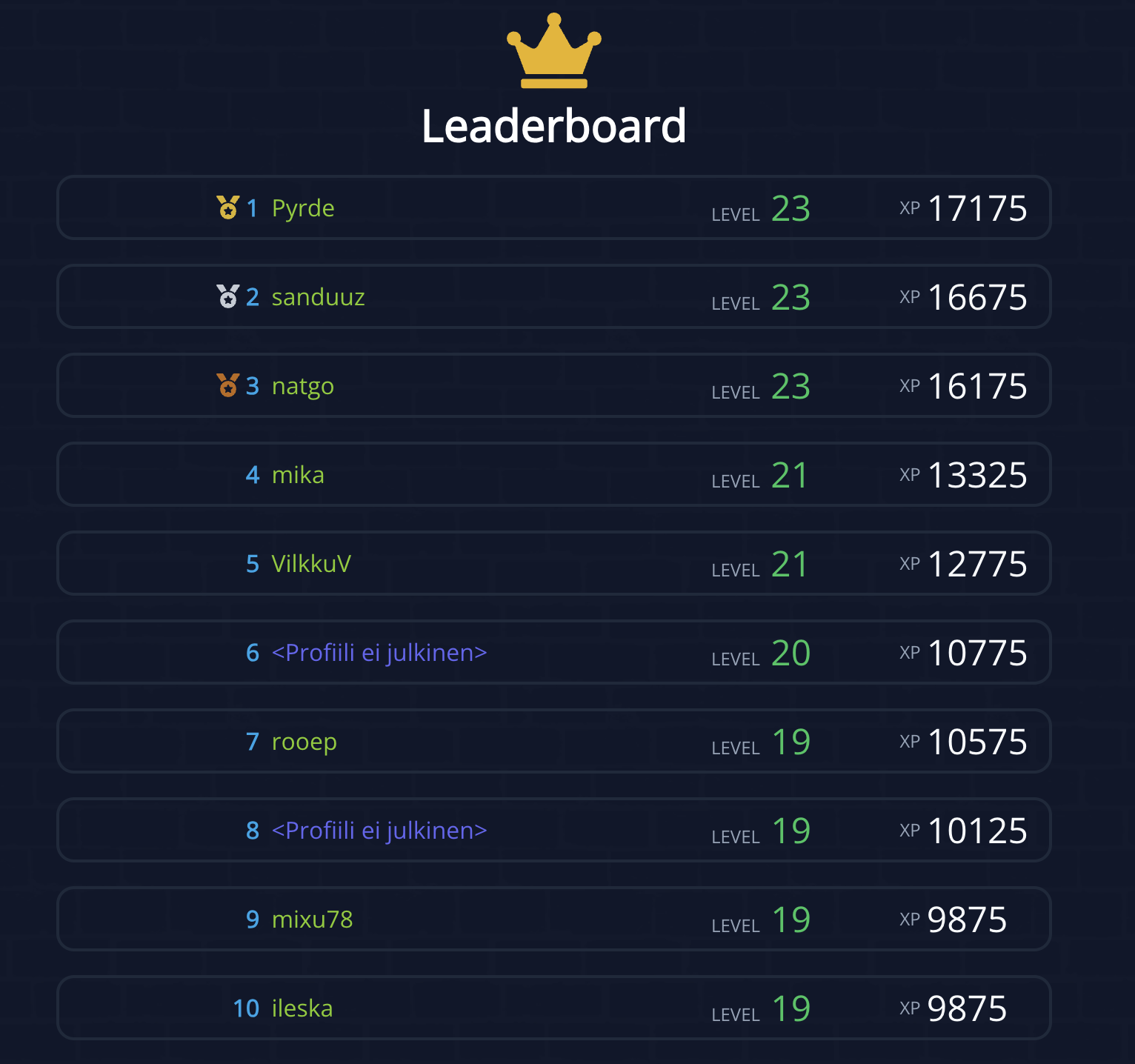
Compete on the leaderboard
Compete on the leaderboard against other students.
Keep up your streak
A long streak of completing tasks increases your streak.
Get badges
By completing challenges you get badges.
No VPN required
Real-world lab exercises brought straight to your browser
Hakatemia lab environment has used a variety of technologies to optimize the user experience. We always strive to provide the simplest, most functional and fastest user interface for completing the task.
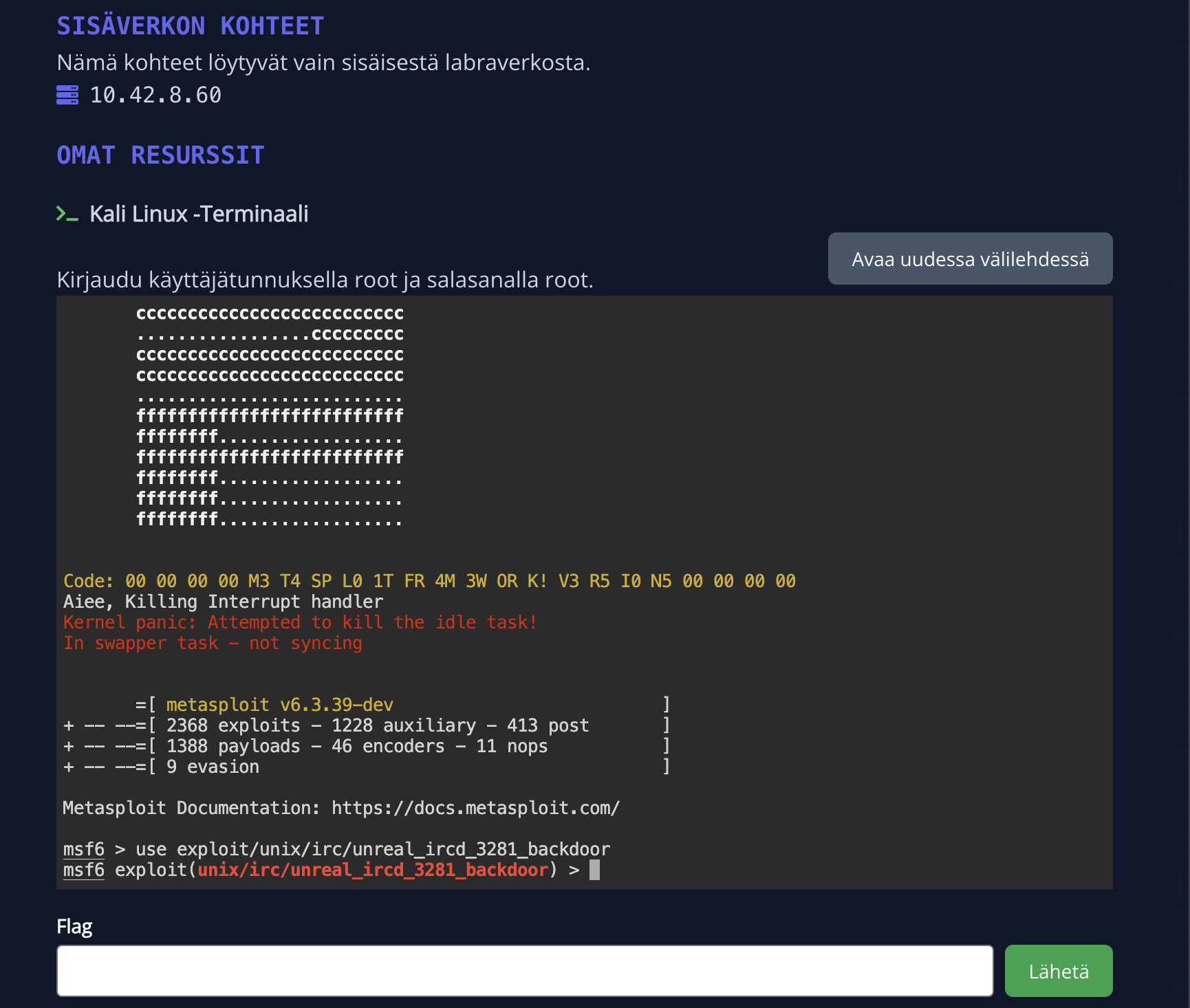
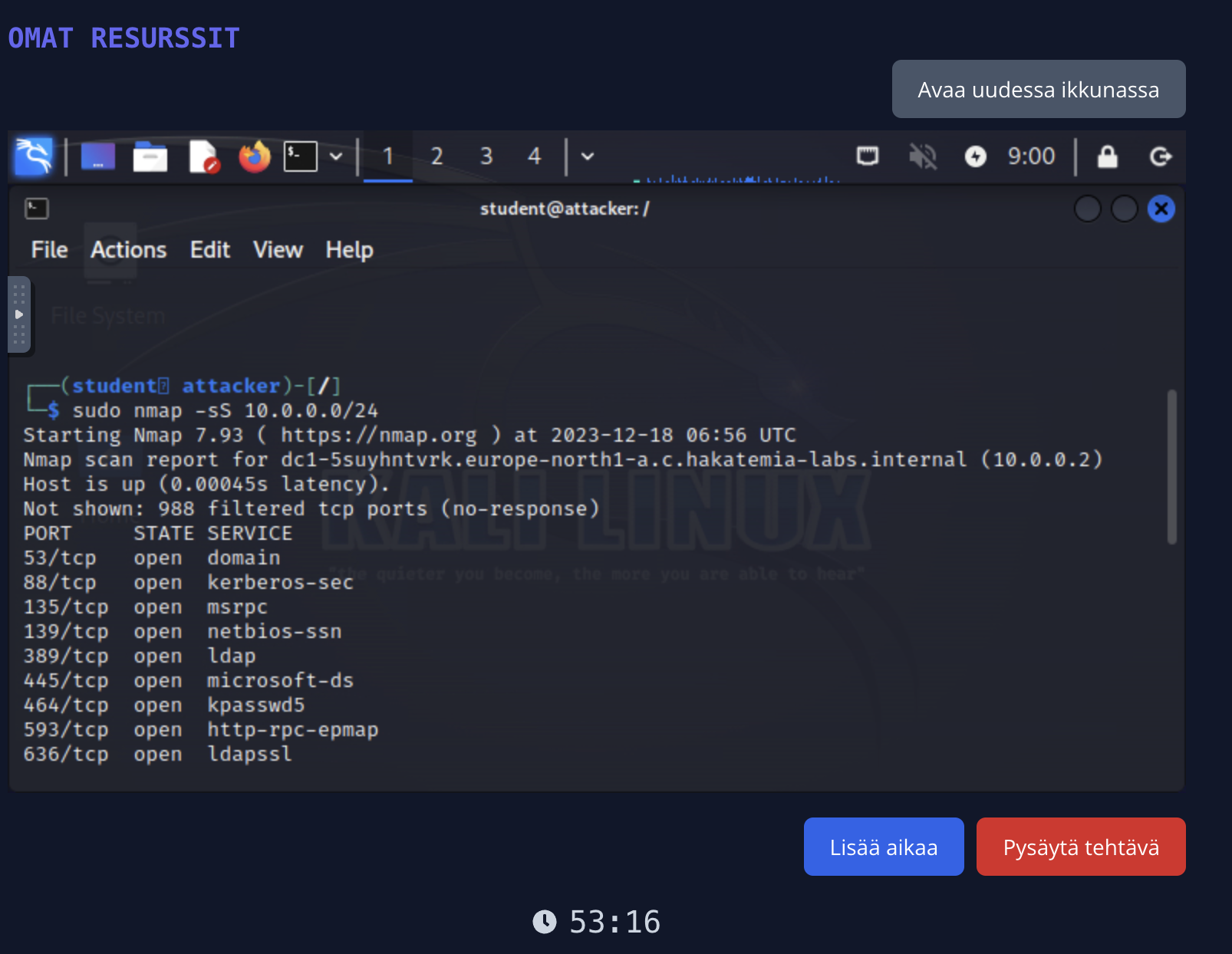
Web-based terminal
Often lab exercises do not require a full desktop environment, but rather a terminal. For this reason, Hakatemia uses a terminal based on xterm.js, which works directly in your browser. Unlike a full remote desktop, the web terminal works in real time even on slower connections and copy/paste works normally.
Web-based desktop
However, some lab exercises require a full desktop environment. In this case, we use a VNC connection tunneled over WebSockets, which allows a fully functional Kali Linux desktop directly in your browser.
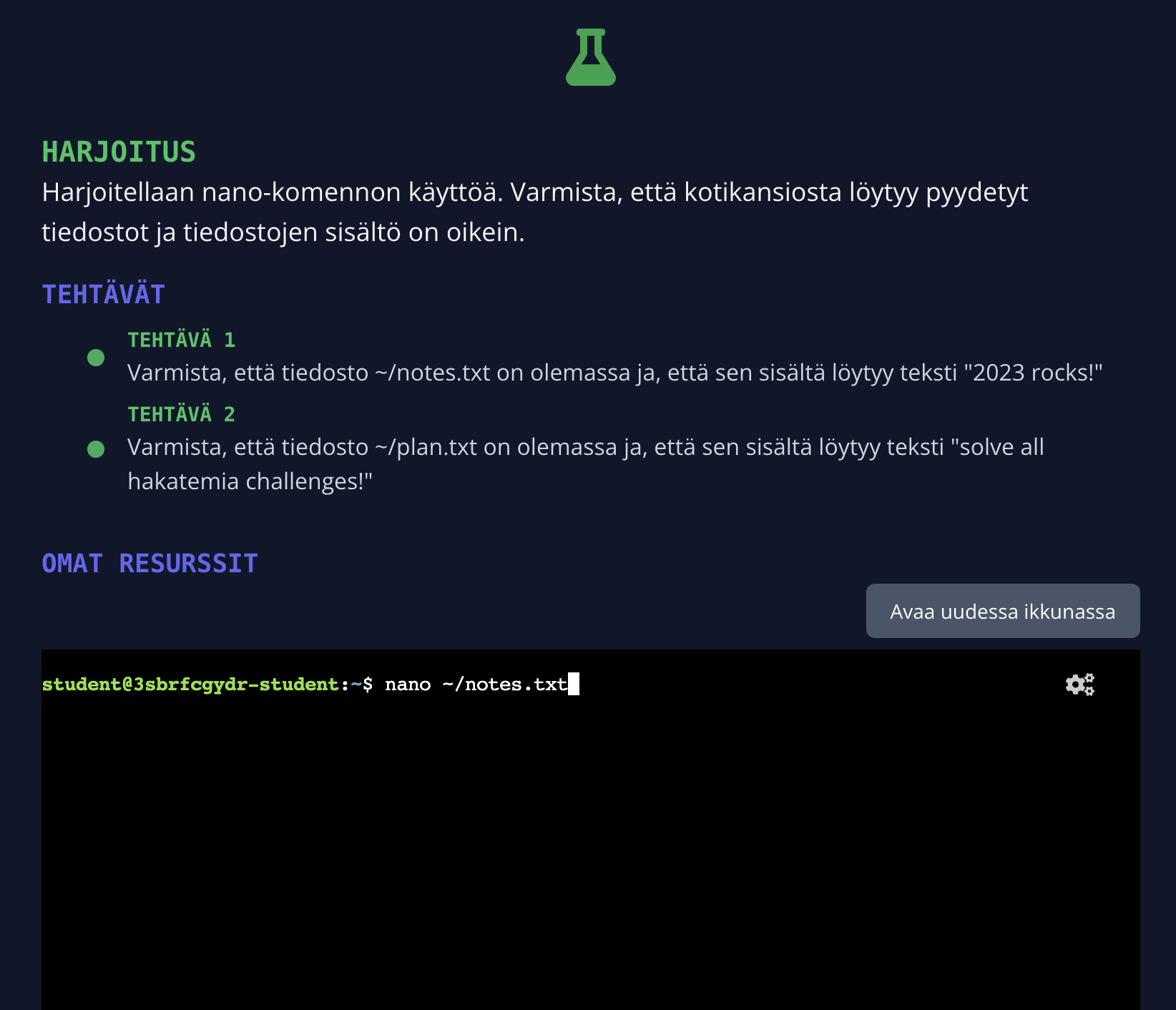
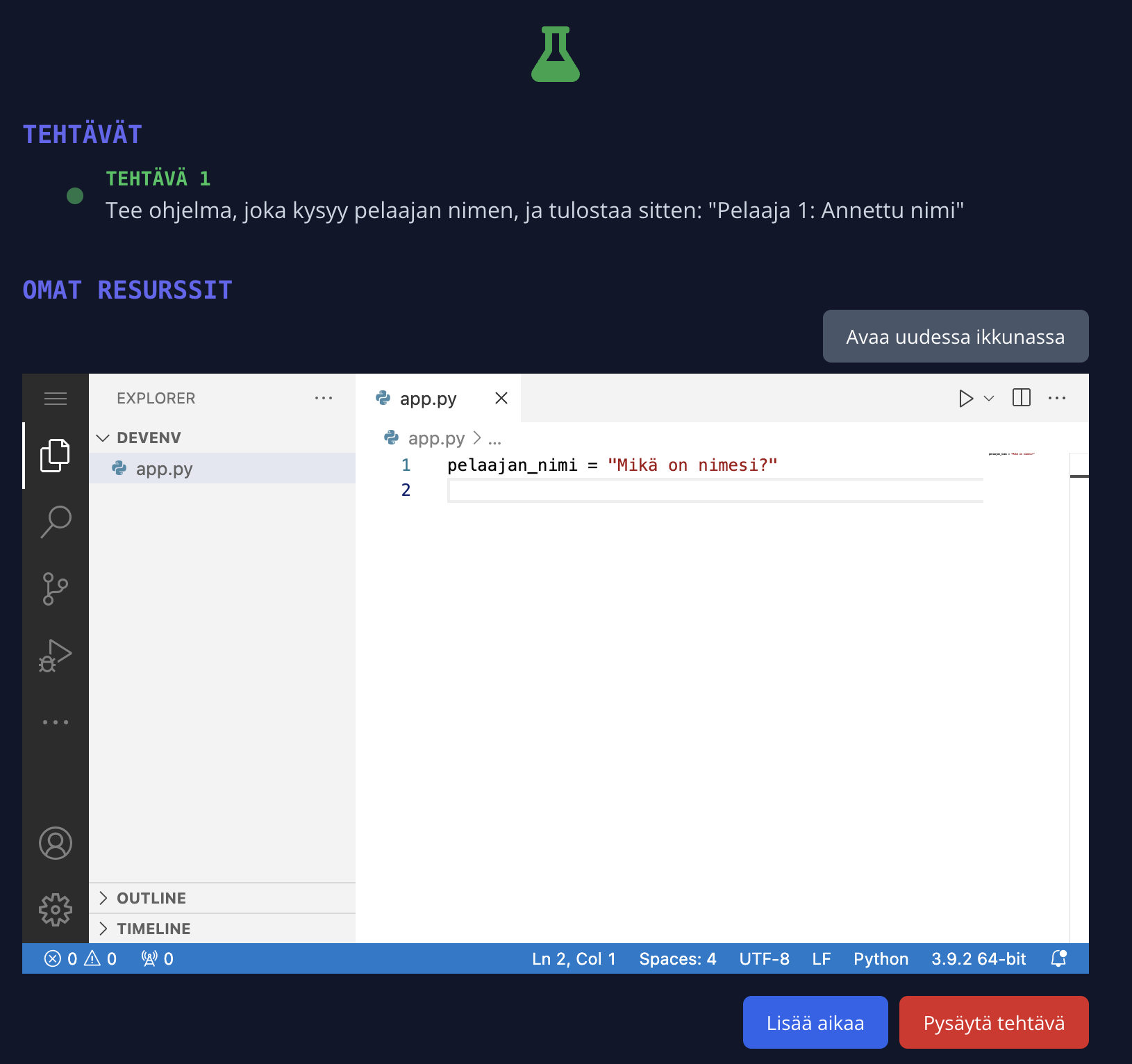
Web-based development environment
In the web development environment, you can write and run code and scripts directly in your browser. This option is typically used when you are required to write or edit code or scripts to complete the task.
Practice attacks and earn experience points
How does Hakatemia work?
On a regular learning platform, you watch videos, read texts, and complete assignments. These basic elements are also found in Hakatemia, but they are all just preparation for the core of Hakatemia: lab exercises. In Hakatemia labs, you get to perform attacks against real vulnerable targets and earn levels and experience points when you solve a task.
- Watch video.
- Many courses or modules have a video where the topic is covered.
- Read material.
- All modules include readable material consisting of text, images, questions, and exercises.
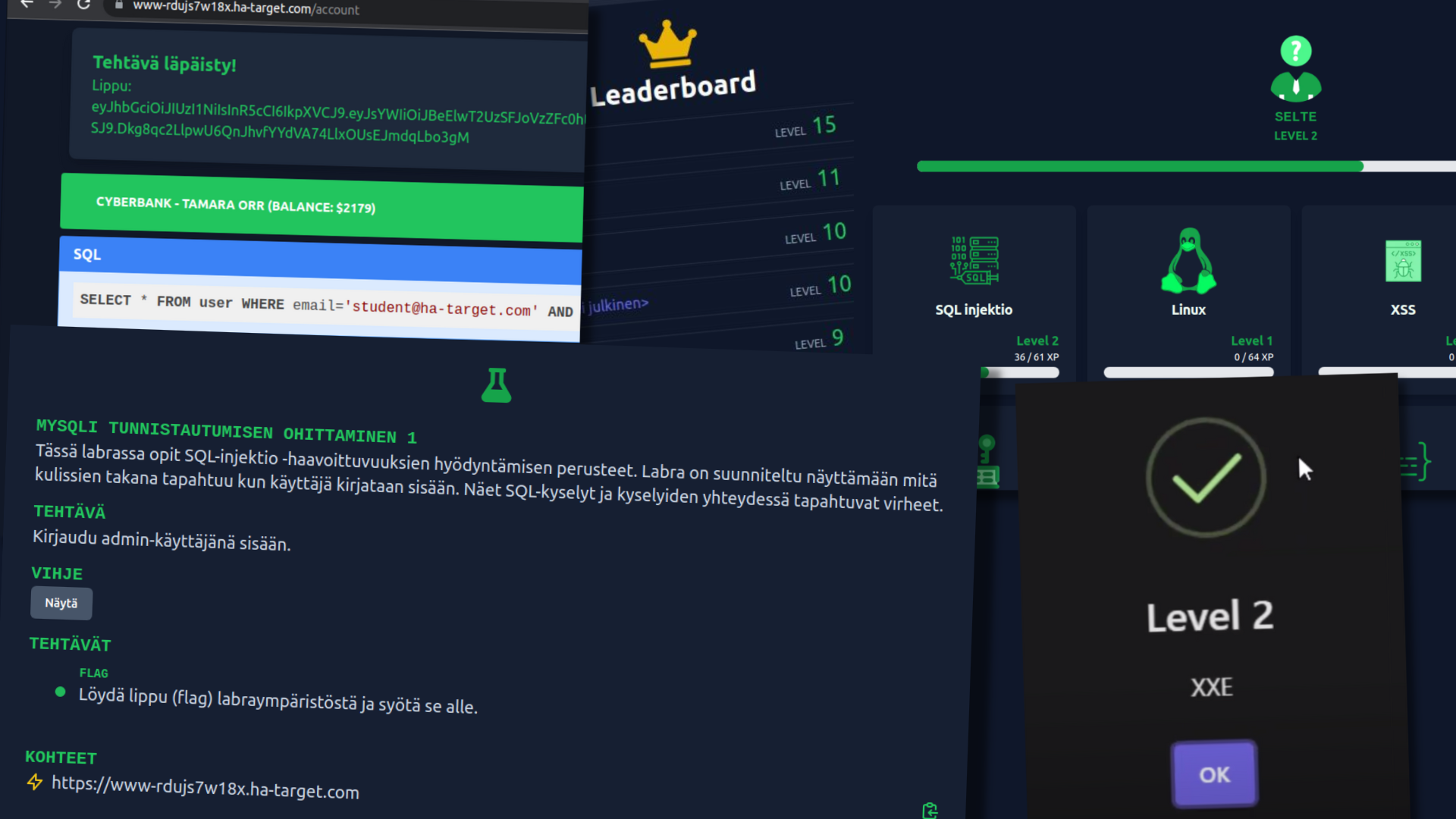
- Start lab task.
- You will be given your own server in a few seconds, where you will find a vulnerable web application. You are free to search for and exploit vulnerabilities in the application. Depending on the task, you will also have access to attacker resources, such as a Kali Linux terminal that opens in your browser, where you can run attack tools and receive connections.
- Use tools.
- As a Hakatemia PRO member, you will also have access to Hakatemia tools that make it easier to find and exploit vulnerabilities.
- Enter flag on Hakatemia page.
- When you complete a task, you will receive a flag from the lab environment. When you enter the flag on the Hakatemia page, you will earn experience points and progress in the course.
- Climb the leaderboard.
- Hakatemia has a leaderboard that always lists the top ten hackers in Hakatemia with their levels and experience points.
Latest additions

Computer Networks - Practice the Learned Material

Levels 2

Levels 1

Forum

Cryptography - Learned Practice

Icecream summer

Securing Linux - Practice what you've learned

Using a firewall in a linux environment
Blog
Metasploit, that pentester's swiss army knife
Sunday 22.10.2023
Welcome to Hakatemia's latest course! Metasploit is a popular attack framework that helps professionals identify and exploit security holes. In this course, you will go through the use of Metasploit and learn how it can be used to carry out attacks and find security holes.